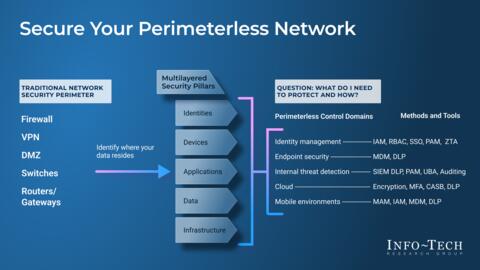
This storyboard redefines traditional network security practices around controlling access to the network. It highlights the need for a security strategy that focuses instead on your protect surfaces.
Unlock Storyboard
Get Instant Access
Our systems detected an issue with your IP. If you think this is an error please submit your concerns via our contact form.