- Agencies struggle to comply with evolving CJIS mandates while managing modern IT systems.
- Lack of security/compliance teams hinders implementation and upkeep of CJIS controls.
- Cloud and hybrid adoption create audit and interoperability challenges.
- Limited funding and complex audit requirements lead to restricted access and failed audits.
Our Advice
Critical Insight
Agencies that embed compliance into day-to-day operations, rather than treating it as a one-time requirement, are better positioned to reduce risk, pass audits, and maintain secure, uninterrupted access to critical justice data.
Impact and Result
- Develop a structured CJIS security compliance management framework that simplifies governance, aligns with evolving standards, and supports multiagency coordination.
- Provide tools and templates to improve audit readiness, standardize access controls, and enhance visibility across IT environments.
- Promote long-term compliance through continuous monitoring, automated reporting, and clear guidance for integrating CJIS policies into modern IT infrastructures.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
8.0/10
Overall Impact
$6,800
Average $ Saved
5
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Morrison County
Guided Implementation
8/10
$6,800
5
I was able to talk to experienced staff that have dealt with implementing this program previously.
Build a CJIS Compliance Program
Ensure compliance and readiness for CJIS modernization and audits.
Analyst perspective
Unify compliance to maximize operational efficiency.

As digital infrastructure expands and security demands evolve, Criminal Justice Information Services (CJIS) compliance has become foundational to effective law enforcement and government operations. Compliance is no longer a static requirement – agencies must adapt to a dynamic landscape of threats, technologies, and interagency coordination.
Agencies at all government levels navigate complex environments with varying capabilities and constraints. Fragmented systems, inconsistent policy enforcement, and siloed data practices often lead to inefficiencies, duplicative work, and audit fatigue. In the absence of a common structure, compliance efforts can become burdensome, slowing down response times and increasing operational costs.
Efficiency in compliance begins with shared direction. Centralized governance, standardized controls, and coordinated audit management empower agencies to manage resources more effectively while maintaining alignment with national standards. Cross-jurisdictional collaboration and scalable tools help ensure consistency without compromising flexibility.
A unified compliance framework enhances visibility, eliminates redundancy, and supports faster, smarter decision-making across the public safety ecosystem. When agencies work from a common foundation, they are better equipped to operate securely, efficiently, and with greater agility.
Vidhi Trivedi
Research Analyst, Government Industry
Info-Tech Research Group
Executive summary
Your Challenge
- Law enforcement and government agencies face mounting pressure to comply with evolving CJIS security mandates while managing modern IT operations.
- Most agencies lack dedicated security or compliance teams, making it difficult to interpret, implement, and maintain complex and frequently updated CJIS requirements.
- As organizations adopt hybrid and cloud-based systems, they struggle with interoperability, limited funding, and growing audit requirements, leading to delayed investigations, failed audits, and restricted access to national criminal justice databases.
Common Obstacles
- Many agencies fall behind on implementing required security updates like multifactor authentication (MFA) and encryption due to limited expertise and staffing.
- Fragmented IT environments, spread across on-premises, cloud, and hybrid systems, make it difficult to apply consistent compliance controls and configurations.
- Budget constraints delay essential upgrades and audit readiness, increasing the risk of noncompliance, data breaches, and operational disruptions.
Info-Tech’s Approach
- Develop a structured CJIS security compliance management framework that simplifies governance, aligns with evolving standards, and supports multiagency coordination.
- Provide tools and templates to improve audit readiness, standardize access controls, and enhance visibility across IT environments.
- Promote long-term compliance through continuous monitoring, automated reporting, and clear guidance for integrating CJIS policies into modern IT infrastructures.
Info-Tech Insight
Agencies that embed compliance into day-to-day operations, rather than treating it as a one-time requirement, are better positioned to reduce risk, pass audits, and maintain secure, uninterrupted access to critical justice data.
Your challenge
Agencies must maintain CJIS compliance, but most are not equipped to keep up.
- Compliance is complex and constantly changing. CJIS policies are regularly updated with new encryption standards, access control requirements, and audit expectations. Most agencies lack the resources or visibility to keep pace, especially as data attribution and cloud integration become more central to compliance. What was secure yesterday may no longer meet today’s standards.
- Teams are underresourced and overextended. Many law enforcement organizations do not have dedicated compliance or cybersecurity personnel. General IT teams are left to interpret and implement nuanced federal requirements, often resulting in misconfigurations, inconsistent enforcement, and missed deadlines for mandated updates.
- Modernization introduces new risks. As agencies shift toward cloud and hybrid environments, existing systems and processes become harder to govern. Inconsistent configurations and interoperability gaps can delay investigations, trigger audit failures, or even cut off access to national justice databases.
Pinpoint what is breaking CJIS compliance
Adapting to Evolving Security Policies
- Challenge: CJIS policy updates require agencies to continuously adjust encryption, access controls, and audit procedures, which strains time and resources.
- Impact: Falling behind leads to security risks, failed audits, and restricted access to national law enforcement databases.
Managing Compliance in IT Environments
- Challenge: Agencies working across on-premises, cloud, and hybrid systems struggle to align CJIS requirements across all platforms.
- Impact: Misconfigurations and inconsistent controls increase the risk of data breaches and compliance failure.
Ensuring Secure Data-Sharing Across Agencies
- Challenge: Seamless collaboration between local, state, and federal law enforcement requires strict CJIS-compliant controls for shared systems.
- Impact: Gaps in interoperability can delay or block access to critical justice data.
Lack of Dedicated Compliance Teams
- Challenge: Many agencies rely on general IT staff with limited cybersecurity or compliance expertise.
- Impact: Poor enforcement of CJIS controls results in failed audits, unauthorized data access, and weak breach response.
High Cost of Compliance and Audit Preparation
- Challenge: Compliance demands investment in secure infrastructure, audit tools, and staff training, which strains tight budgets.
- Impact: Funding gaps lead to deferred upgrades, increased risk of cyberattacks, and audit failure.
Common obstacles
Inconsistent practices and limited capacity put CJIS compliance at risk.
- Frequent policy updates create a moving target. CJIS compliance is not static. As new policies introduce requirements like MFA, data attribution, and encryption protocols, many agencies lack the resources or awareness to keep up. Without a consistent update process, even well-intentioned teams fall out of compliance, risking failed audits and access restrictions.
- Fragmented systems undermine consistency. Agencies often operate in complex IT environments, juggling on-premises, cloud, and hybrid systems. Each platform requires tailored configurations to meet CJIS standards. Without integrated controls and standardized processes, even minor misconfigurations can create serious security gaps.
- Limited staffing and budget strain enforcement. Many organizations lack dedicated compliance officers or cybersecurity personnel. General IT teams are expected to interpret and apply detailed CJIS policies with limited guidance, while budget constraints delay necessary investments. As a result, teams operate reactively, often addressing issues only after compliance has already been compromised.
“CJIS is not a separate thing – it’s part of what we should already be doing with good data governance. But it needs to be built into every workflow, not treated as an afterthought.”
– Michael Murray, Cybersecurity IT Manager, City of Santa Cruz.
Close the gaps before compliance costs you
Noncompliance is not just risky – it’s costly, resource-intensive, and avoidable.
Fragmented CJIS Compliance Across Agencies
The absence of a standardized enforcement approach across federal, state/provincial, and municipal agencies creates inconsistencies in data security, access controls, and audit readiness, increasing the risk of regulatory breaches and cybersecurity vulnerabilities.
Redundant Compliance Efforts and Resource Strain
Overlapping CJIS security mandates with other compliance obligations leads to duplicated compliance tasks, wasted resources, and administrative burdens, making it harder for agencies to streamline security policies and meet evolving regulatory expectations.
Severe Consequences of Noncompliance
Failure to adhere to CJIS security policies can result in fines, revoked access to national law enforcement databases, increased cybersecurity threats, and reputational damage, undermining law enforcement operations and public safety efforts.
Noncompliance comes at a high cost, and it’s rising.
The price of falling behind on compliance is steep. “The biggest cost amplifiers were security system complexity, security skills shortage, and noncompliance with regulations.”
Source: (IBM, 2023)
Noncompliance can multiply financial risk: “Organizations with a high level of noncompliance with regulations showed an average cost of US$5.05 million, which exceeded the average cost of a data breach by US$560,000, a difference of 12.6%.”
Source: (IBM, 2023)
Info-Tech’s approach
Turn CJIS compliance into a sustainable and proactive process.
- Structured frameworks. Info-Tech guides agencies through a structured CJIS compliance management framework that simplifies governance, aligns with FBI standards, and supports consistent policy implementation across departments, systems, and vendors.
- Built-in audit readiness. Info-Tech’s tools help agencies operationalize CJIS requirements, such as MFA, data encryption, access control, and logging, by embedding them into daily workflows. This ensures teams are prepared not just for scheduled audits but also for real-time threats or investigations.
- Support for hybrid IT environments. Whether on-premises, cloud, or hybrid, Info-Tech’s approach helps agencies identify and address gaps in configuration, interoperability, and documentation. Info-Tech provides tailored guidance to ensure secure system integration and uninterrupted access to national justice databases.
Shift from ad hoc to continuous CJIS compliance
CJIS compliance is not a one-time milestone, it is a moving target. Security frameworks such as CJIS, the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF), and Federal Risk and Authorization Management Program (FedRAMP) are crucial to follow for compliance and are continuously evolving, and law enforcement agencies must adapt quickly to stay prepared for audits. Yet most agencies lack the tools, structure, and bandwidth to track these changes and translate them into everyday operations.
In this dynamic environment, even well-documented standards become difficult to apply. From interpreting policy updates to enforcing secure workflows across hybrid systems, the burden on IT and compliance teams continues to grow.
59% of security and IT leaders indicate their organizations must comply with multiple regulatory frameworks, including CJIS.
Source: (Coalfire, 2023)
76% of risk and compliance professionals say that building and maintaining a culture of compliance is an essential priority for their organization’s decision-making.
Source: (Navex, 2023)
58% of security and IT professionals indicated the need for larger compliance budgets, highlighting the resource demands of maintaining standards such as CJIS.
Source: (Coalfire, 2023)
Build and operationalize a CJIS compliance framework
CJIS compliance requires more than documentation – it requires structure, strategy, and sustainable execution.
Your Challenge
Agencies face increasing pressure to comply with CJIS but lack the structure to make it sustainable. Evolving mandates such as MFA, access logging, and encryption require constant adaptation. Many agencies lack the internal expertise, time, or clarity to translate policy into practice.
Compliance missteps carry high stakes. Without a clear governance model, agencies risk delayed investigations, data exposure, and restricted access to national justice systems, compromising operational integrity and public safety.
Common Obstacles
Skill shortages leave generalist IT teams struggling to interpret and enforce specialized CJIS controls.
Complex environments such as on-premises, cloud, and hybrid systems make it difficult to apply consistent configurations and track compliance status.
Limited funding delays critical upgrades and prevents agencies from automating compliance processes and preparing effectively for audits. This increases the likelihood of security breaches and noncompliance.
Info-Tech's Approach
Develop a structured CJIS compliance framework that helps agencies align with evolving federal standards while simplifying governance across systems and teams.
Standardize access controls, audit procedures, and encryption practices to streamline policy implementation across on-premises, cloud, and hybrid environments.
Sustain compliance through automated monitoring, continuous reporting, and practical guidance that embeds CJIS controls into daily operations.
Is this research right for you?
Consider whether you should use a governance, risk, and compliance (GRC) tool or an Excel tool.
- This research offers Excel and Word-based tools to help organizations manage their security compliance obligations.
- Excel spreadsheets are an excellent way of managing compliance data, up to a point.
- Organizations that have more complex structures and more compliance requirements should consider the use of a special GRC tool.
- This research product may still help you establish your security compliance program even if you opt to use a GRC tool rather than the Excel tool provided.
Operational Environments
Organizations with more than five separate operational environments should consider a GRC tool.
Compliance Obligations
Organizations with more than ten security and privacy/data protection compliance obligations should consider a GRC tool.
CAD deliverables
Each step of this CAD is accompanied by supporting deliverables to help you accomplish your goals:
Security Compliance Process Template
A structured template that helps organizations establish, implement, and track security compliance to meet policy and business needs.
Information Security Program Gap Analysis Tool
A template that helps organizations assess control maturity and identify compliance gaps.
Key deliverable
CJIS Security Compliance Management Tool
The CJIS Security Compliance Management Tool is a compact GRC system in a convenient spreadsheet.
Info-Tech’s methodology to build a CJIS compliance program
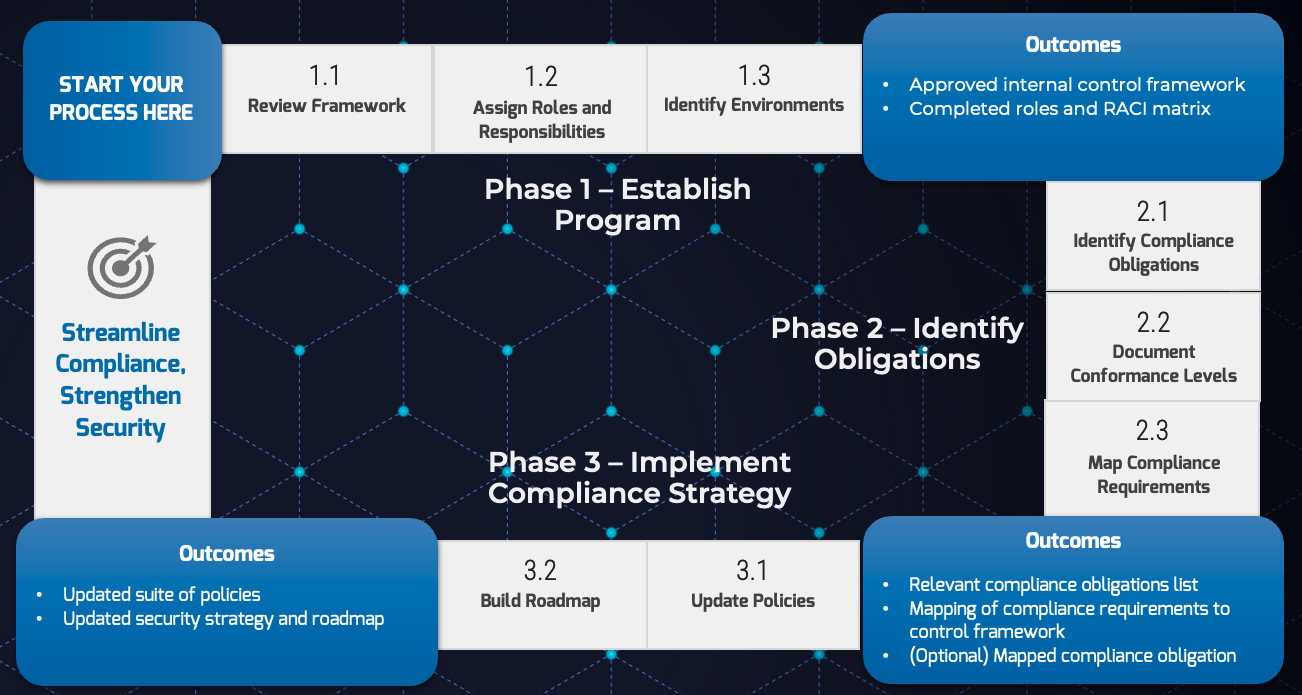
Phase Steps |
1. Establish Program1.1 Review framework 1.2 Assign roles 1.3 Identify environments |
2. Identify Obligations2.1 Identify compliance obligations 2.2 Document conformance levels 2.3 Map requirements |
3. Implement Compliance Strategy3.1 Update policies 3.2 Develop a strategy and roadmap |
Phase Outcomes |
|
|
|
Insight summary
Streamline Compliance, Strengthen Security
A control framework is the first key to cost-effective compliance. It enables you to meet multiple requirements by validating one control across several obligations.
Set Clear Boundaries, Minimize Risk
Environments are the second key to cost-effective security compliance.
Environments allow you to apply a scope to your CJIS compliance obligations and minimize your compliance costs.
Invest Where It Matters Most
Conformance levels are the third key to cost-effective security compliance.
Conformance levels allow your organization to make informed business decisions on how compliance resources will be allocated.
Audit-Ready, Always
Audit readiness is the final key to cost-effective security compliance.
Take charge of your audit costs by preparing test scripts and evidence repositories in advance.
Compliance Risk vs. Security Risk in CJIS
Compliance risk in CJIS relates to legal penalties, database access restrictions, and operational disruptions due to noncompliance. Security risk involves cyberthreats, data breaches, and unauthorized access to criminal justice information. While CJIS mandates enforce security best practices, noncompliance increases both regulatory and cybersecurity vulnerabilities, putting law enforcement data and public trust at risk.
Project benefits
IT benefits
- Reduces complexity within the control environment by using a single framework to align multiple compliance regimes.
- Reduces costs and efforts related to managing IT audits through planning and preparation.
- Improves information security practices through self-assessments.
Agency benefits
- Provides senior management with a structured framework for making business decisions on allocating costs and efforts related to cybersecurity and data protection compliance obligations.
- Reduces compliance risk.
- Enables better visibility into compliance status.
Measure the value of this project
Efficient compliance today protects security, reduces costs, and ensures operational success tomorrow.
Consider tracking the following metrics to measure the value of your CJIS compliance management program.
Metric |
Expected Improvement |
| Number of security controls required for compliance policies | Implementing a standardized compliance framework may reduce the number of required controls by 25-50%, improving efficiency. |
| Control implementation costs | Use of conformance levels may lower implementation costs by 25% per security control, reducing financial strain. |
| Control maintenance costs | Using predefined compliance environments for CJIS security measures can reduce maintenance costs by 25-50%, minimizing long-term expenses. |
| Audit costs | Streamlined audit preparation through automated evidence tracking and standardized security protocols may reduce audit costs by up to 50%. |
| Compliance management efforts | Effort required for overall compliance management may reduce by 25% or more, freeing resources for other critical operations. |
Case study
A state agency developed a CJIS compliance program to improve audit readiness and streamline data governance.
Department of Corrections: Washington State
INDUSTRY
Government
SOURCE
Washington State Department of Corrections, Info-Tech Engagement
Challenge
State agencies often face mounting pressure to meet CJIS compliance standards amid changing audit expectations and limited internal resources. Without a dedicated tool or framework, many organizations struggle to interpret evolving policies, track maturity, and prepare for recurring audits.
One Washington-based agency found itself in this position. With no centralized compliance tracking in place and little clarity from state directives, the agency’s cybersecurity and compliance teams needed a way to proactively manage CJIS requirements. They partnered internally to build a tailored compliance framework and close critical gaps.
Solution
The agency began by designing a gap analysis to identify and align key CJIS controls with their existing cybersecurity framework. They leveraged the Varonis data security platform to locate sensitive files, automate access audits, and eliminate outdated file sharing systems.
Over time, the agency matured its compliance posture by integrating CJIS controls with broader governance efforts, developing a centralized audit program, and aligning cloud usage with federal expectations. The team also implemented internal checks to ensure ongoing conformance with Washington state law and NIST Cybersecurity Framework (CSF) guidelines.
Results
The compliance framework enabled the agency to complete its annual CJIS audit successfully and significantly reduced the time and effort needed for future audits. It improved data classification, minimized policy violations, and clarified ownership across departments.
This structured approach enhanced the agency’s overall resilience by embedding CJIS compliance into everyday operations, supporting both regulatory alignment and long-term cybersecurity maturity.
Info-Tech offers various levels of support to best suit your needs
DIY Toolkit
"Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful."
Guided Implementation
"Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track."
Workshop
"We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework in place."
Executive & Technical Counseling
"Our team and processes are maturing; however, to expedite the journey we'll need a seasoned practitioner to coach and validate approaches, deliverables, and opportunities."
Consulting
"Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project."
Diagnostics and consistent frameworks are used throughout all five options.
Guided Implementation
What does a typical GI on this topic look like?
Phase 1
|
Phase 2
|
Phase 3
|
